Online scams and spam have reached an unprecedented limit today. Phishing attacks are perhaps one of the most common types of attacks that we have been witnessing. Even among the different phishing attacks observed, specific ones have become more dangerous. One such phishing attack that businesses need to be safer from, would include Spear Phishing. Let us check out what is Spear Phishing and how to prevent Spear Phishing from attacking you.
Spear Phishing is a specific form of attack that is aimed at some particular organizations and individuals to steal sensitive information or get access to their computer systems. This type of attack belongs to the category of Social engineering tactics and makes use of real-looking email – just like in the case of other phishing attacks.
Spear Phishing – The Overview and Definition
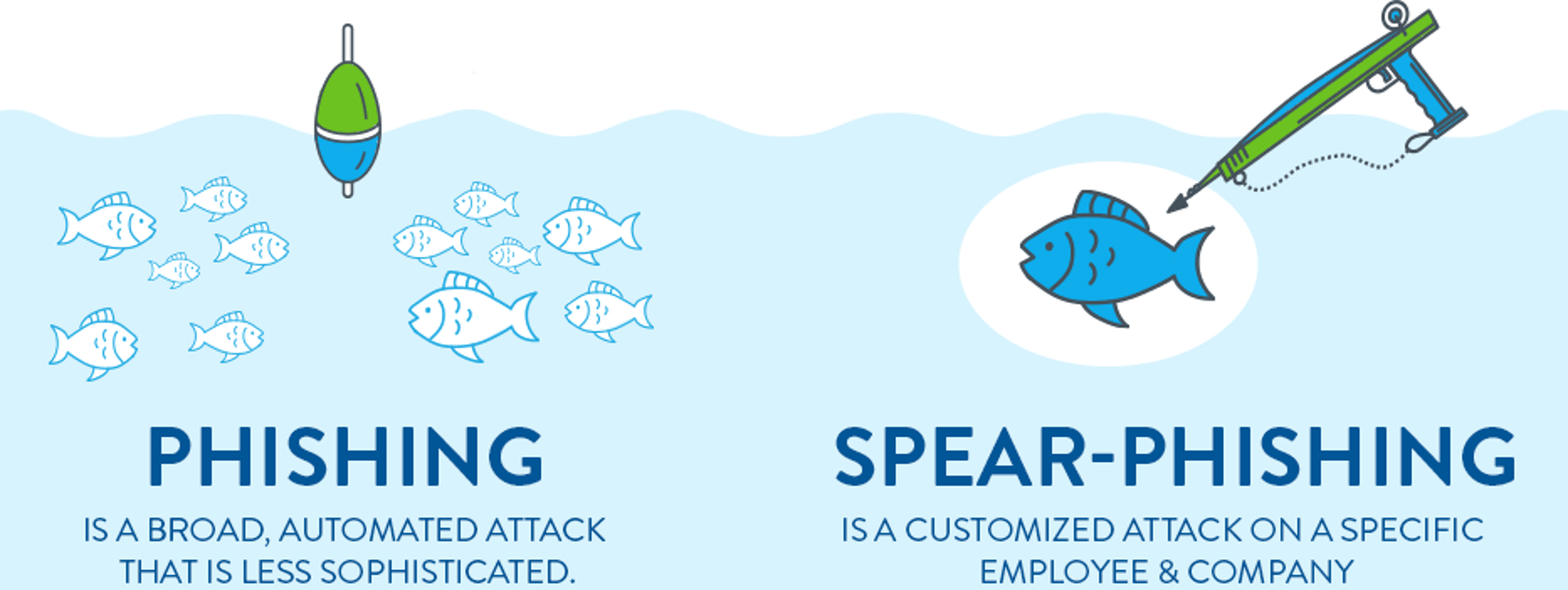
Phishing is a general term used for cyberattacks carried out by email, SMS, or phone calls. Other phishing attacks are generalized and are targeted at any general organization. These attacks are meant to seek unauthorized access to sensitive information. However, Spear Phishing is targeted at specific individuals or organizations, in contrast to general phishing attacks.
The phishing attacks, in general, make use of emails and other contact mechanisms that appear to be coming from reliable sources such as PayPal, Google, and alike. In the case of Spear Phishing, the emails appear to be coming from someone within the organization. For instance, the mail may look like the one being sent by the CEO to one of the employees, asking to share some information.
For example, Once I received an email from a scammer who pretended quite well to be from PayPal, but as I checked closely, it was misspelled as “Paypl” in his email. I understood that this is a phishing attack, and can be categorized as Email Spear Phishing. Sometimes they may even spoof the email address but remember there is always something out there that you can find out. So, when you receive some unexpected email even if it looks like from a real and authentic source, try to carefully check everything like the email address, the links included in the email, etc. Never click those links directly, you can just copy those links paste them into Notepad, and investigate if they look authentic.
The success of Spear phishing lies in the fact that it appears to be arriving from someone trusted within the organization and someone the recipient may personally know. The details in the mail are not vague but may have a higher level of validity. A few possible targets of the Spear phishing are generally high-level executives and decision-makers, IT professionals and other technical staff, employees with access to sensitive information, and public figures and celebrities.
Phishing Vs. Spear Phishing
| Aspect | Phishing | Spear Phishing |
|---|---|---|
| Targeting | Broad and non-specific, targeting many people | Highly targeted, focusing on specific individuals |
| Attack Method | Typically uses generic messages and templates | Tailored and personalized messages for the victim |
| Email Content | Often contains generic or vague information | Contains specific details about the victim or company |
| Sender Impersonation | May impersonate well-known organizations | Often impersonates someone the victim knows closely |
| Goal | Generally aims to steal login credentials | May seek sensitive company or personal information |
| Prevalence | Widespread and sent to a large number of people | Less common and sent to a small, select group |
| Examples | Fake bank login page, lottery scam emails | Impersonating a CEO to request wire transfers |
| Risk Level | Lower risk as it relies on casting a wide net | Higher risk due to the personalized and targeted approach |
| Countermeasures | Email filtering, user education, security software | Requires more advanced security measures and employee training |
How Does Spear Phishing Work?
Spear Phishing does not begin focused on blind targets. It will start with complete research into the target organization. The attacker researches the target and gathers information such as their email address, job title, and other details. Once that is done, the attacker crafts a message that is convincing enough, impersonating a higher-up in the organization, a trusted source, a colleague, or a business partner.
The message can include specific call-to-action elements. A few of these options include a link or a download. Once the target clicks on the attachment or downloads it, the malware is installed on the computer. This will ultimately complete the action that the attacker is looking for – like having access to the sensitive information or, in certain extreme cases, the hacker taking over the entire target computer.
Multiple Types of Spear Phishing
Spear Phishing can be achieved in multiple ways. Some specific types of Spear Phishing can include:
- Email Spear Phishing: This involves the most common Spear phishing attack. You will receive a convincing email that looks as if it has come from a trusted source, like a business associate or a colleague. In most cases, the mail appears to be coming from a higher source in the organization.
- Social media spear phishing: Social media spear phishing involves the use of social media profiles for conning the targets. The attacker creates fake profiles that appear to be coming from trusted sources. The message mostly seems to be legitimate.
- Voice spear phishing: As you might have understood, this involves making phone calls to make the victims divulge confidential and sensitive information. The attacker will pose as if they are talking to you from a legitimate-sounding organization and lure you into providing the information.
- Text message Spear phishing: This involves sending text messages that appear to be arriving from legitimate sources. The message may contain a link for a malicious code, or it may also ask you to download an attachment.
Also Check: Different Types of Scams
How Can You Identify a Spear Phishing Message?
The key to staying safe from a spear phishing attack is to be alert and check the message or mail for any sign of suspicion.
Some of the ways that you can detect a Spear phishing attempt include
Check the email address of the sender
The email address that the message arrives may look precisely similar to the authentic mail, but you would notice a few slight changes and differences. Having a keen eye can help you differentiate the bad from the good. As I shared in an example in this article when a scammer tried to scam me, he pretended to be from PayPal, but it misspelled “PayPl” like this. And, I got to know that this is not a real email.
Check the Errors in Grammar and Spelling.
Spear phishing emails are generally created in a hurry. This will result in spelling and other grammar errors involved. In most of the scenarios, the attackers do not belong to the class of professionals. The email may lack a formal and business tone. This can be an indicator if you look closely enough. Moreover, this may not be the case always because nowadays AI is there so even in a hurry, they can create a well-written email without any grammar and spelling mistakes. So, be careful.
Pay Attention to the Language or Tone.
If you notice a threatening or urgent tone in the email or other message, it is more likely to be the Spear phishing email. You may witness the email threatening you to take legal action if you do not comply. This is yet another clear indicator that the email may be a Spear phishing attempt.
Check Out Suspicious Links and Attachments.
The clear indicator of a Spear phishing email is the links and attachments that may look suspicious. Never click on any link or download the attachments that appear to be unreliable. Before you open any link or download an attachment, make sure that they have arrived from a legitimate and trusted source. To find out the legitimacy, check the email addresses carefully.
What Helps in Preventing Spear Phishing?
There are several ways you can take care of a Spear phishing attempt. Let us check out a few of them to understand the prevention techniques.
Use Reliable Anti-virus Software
Using a trusted anti-virus solution is the first level of defense against the Spear phishing attack. The powerful antivirus solution should be able to protect your device from malware and spear phishing attacks. Ensure that you have kept your antivirus software regularly updated. For example, I am using AVG, and whenever I click on a link that is suspicious, it alerts me every time. This way, I again check on those links, and many times it safeguards me.
Enable Two-Factor Authentication(2FA)
Adding two-factor authentication to your accounts can help you add an extra layer of security to your online presence. There are several forms of two-factor authentication.
Use Complex Passwords
Using passwords that are hard to guess is yet another best option to help you stay protected from spear phishing attacks. It is also advised to change your passwords at regular intervals. This will make it hard for hackers to gain access to your accounts or your online presence.
Closing Thoughts
Spear phishing – in contrast to the regular phishing, is a targeted attempt at breaking into your system and your online information. It involves making you part with the sensitive information and putting your organisation at risk. However, spear phishing attempts are much easy to detect if you are a little alert. Ensure that you have opted for the proper steps against the spear phishing attempts and reduce the risk of being at the receiving end of a phishing attack.







Add Comment